Interpreting Fraud Results
Learn how to interpret the fraud concerns highlighted in your flagged reservations.
If a reservation has been flagged for review, indicating some fraud concerns, it's important to check out the Fraud Detection section of the reservation.
Important note: Your response to fraud concerns/suspicions will depend on your internal business practices and risk tolerance.
Before approving a reservation that's been flagged for fraud, make sure to do your due diligence. That might mean reaching out to the guest to confirm their personal details or setting up an in-person check-in.
Fraud Detection Results:
To give you a complete picture of your guest, we indicate any finding that could suggest fraudulent activity. When examining Autohost's Fraud Detection, you might see one or a combination of these results:
__ online profiles were found
Using the phone number provided by the guest, we pulled up every/any associated online profiles. If this search pulled up zero accounts, it means we weren't able to explore the guest's digital footprint for the sake of verifying their identity.
Email is not deliverable
The email provided does not work, meaning the address cannot receive emails. This guest likely provided a bogus email.
Domain is not registered
The guest provided an email domain (the web address that comes after the @ symbol) that does not exist.
Domain is high risk
Significant malicious activity was confirmed coming from the web domain associated with this guest.
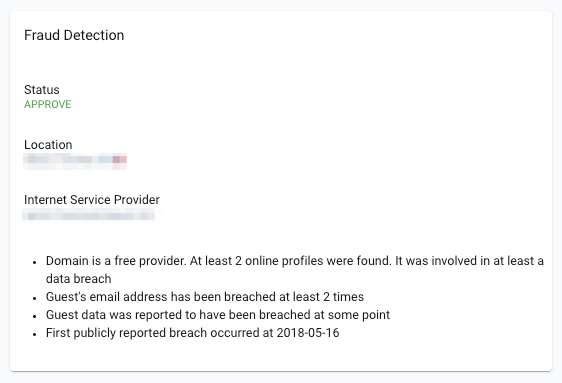
Domain is a free provider. __ online profiles were found. It was/was not involved in __ data breach(es)
This is a combination of different checks to determine: whether the guest is using a free provider (e.g. Gmail, Yahoo!, etc.), how many online profiles the guest has associated with the email provided and if there have been any data breaches.
Domain is a free provider: Each email domain has a different weight in terms of risk level. A free account (that can be opened by anyone) paired with no social profiles might be more suspicious. It could point to phishing/junk email.
Online profiles: The more online profiles attached to the guest, the lower the risk. It means we've been able to validate their ID through social verification.
Data breach: This means the guest's online account has been hacked and their information has been posted online. Email and passwords may have been leaked, in which case the email has been compromised. Someone involved in malicious activity might have access to the guest's email or online accounts. This combined with a flagged (stolen) credit card might suggest fraudulent activity.
Domain is custom and was registered more than __ month(s) ago. __ online profiles were found. It was involved in at least a data breach
A custom domain is a unique branded label that identifies a website. While in most cases, these are attached to company employees, fraudsters can easily purchase domains to mask their identities. That's why the timeframe of the registration is relevant. If the domain was registered recently, there may be cause for concern.
Domain is disposable
Some providers offer temporary email address that are available for a limited amount of time/number of uses. With a disposable domain, the guest is clearly trying to mask their identity. This is highly likely to be fraudulent activity.
Customer is using a datacenter ISP (Internet Service Provider)
A datacenter is a special facility that organizations use to house their critical applications and data. Datacenters are designed to support business applications and data-heavy activities. While this guest could be coming from a commercial location (rather than a home or office), these types of facilities provide users the ability to download massive amounts of information quickly. This could suggest high-tech fraud or a larger fraud operation.
If the reservation shows no other suspicions of fraud, it's likely harmless. Their VPN (virtual private network) might have been flagged because it's hosted in a datacenter ISP.
Customer is using a Web/HTTP/TOR proxy
A proxy hides the user's IP address from the websites they visit, meaning the guest is trying to mask their origin and avoid tracing. While some users implement proxies for security reasons, fraud is commonly associated with proxy connections including: chargebacks, account fraud, spam and more.
There are __ suspicious open ports on the IP address
If a guest is using their phone or laptop at home or at the office, these findings should never come up, unless they have malware. Most of the time it means the user has been infected with a virus, but it could also mean they're the source.
There are more than 2 different IP addresses detected using WebRTC
A normal device doesn’t have two IP addresses, unless connected to multiple networks. This shows the guest is using advanced tools, commonly associated with hacking.
20 or more plugins installed in browser
Multiple plugins (browser extensions) might imply that malware exists. Even plugins that are not malicious can be dangerous, strictly because they have the ability to collect a lot of data about the user, posing threats to privacy.
Cookies are not enabled on user's side
This means the user is avoiding cookie tracking. Some people have these disabled out of privacy concerns, but some are doing so to hide malicious activity. In combination with other fraud concerns, this could be a red flag.
Timezone based on IP geolocation and user's device does not match
The user's browser usually sends the corresponding timezone, unless the IP address is registered somewhere else. The guest might be using a VPN or Tor proxy, which could be legitimate and valid, but might also point to suspicious activity.
Tip: One single fraud concern on its own is likely harmless; a combination of fraud concerns might be more dangerous. Look out for details that don't add up. If the guest says they're traveling for work, but their domain is not registered, that raises suspicions. Why don't they have a work email? Why didn't they book with their work email? It's important to ask yourself these types of questions before making the decision to approve or decline a guest.
